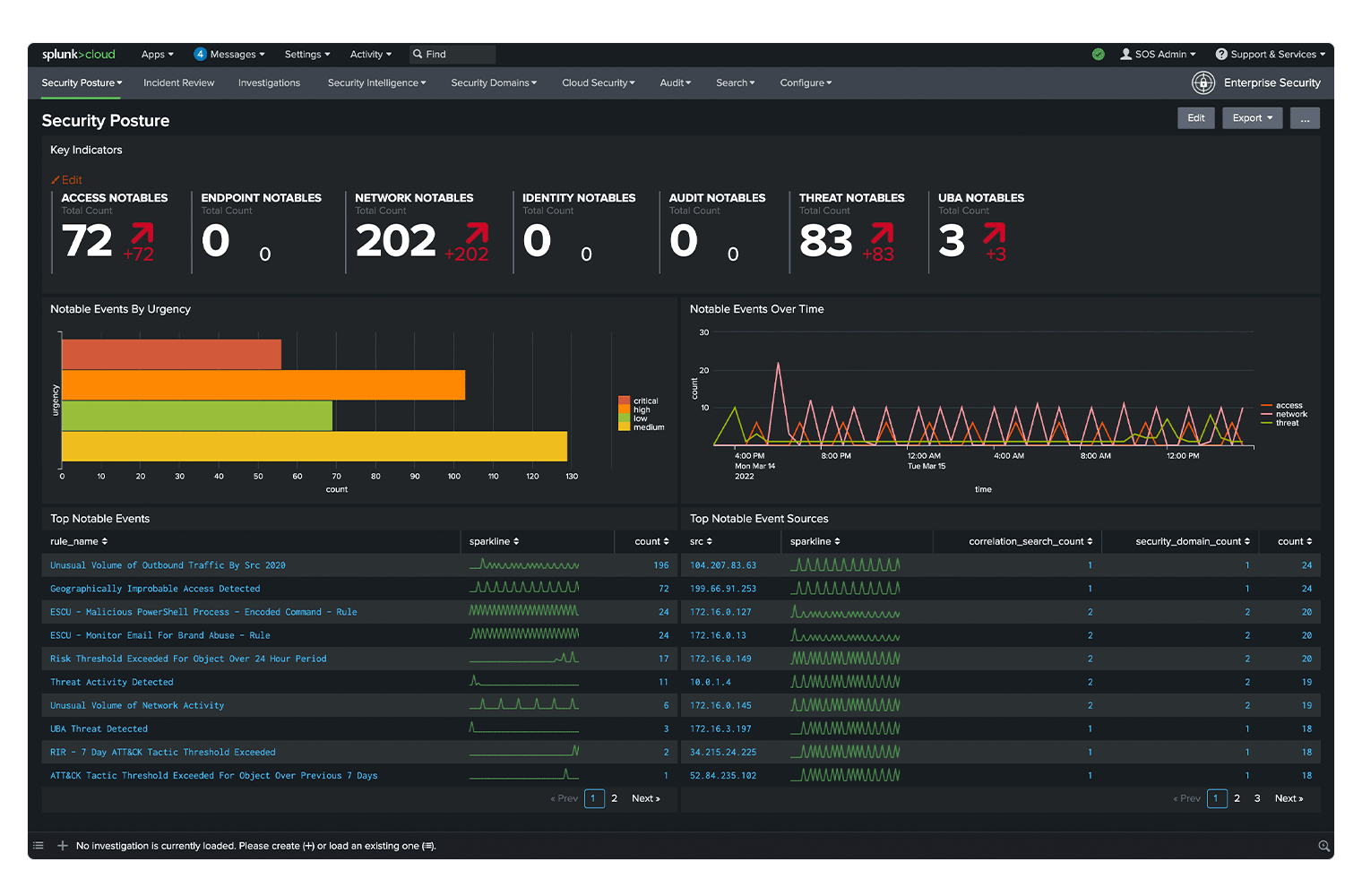
Fast, ML-powered threat detection
Defend against threats with advanced security analytics, machine learning and threat intelligence that focus detection and provide high-fidelity alerts to shorten triage times and raise true positive rates.
Full visibility across your environment
Break down data silos and gain actionable intelligence by ingesting data from multicloud and on-premises deployments. Get full visibility to quickly detect malicious threats in your environment.
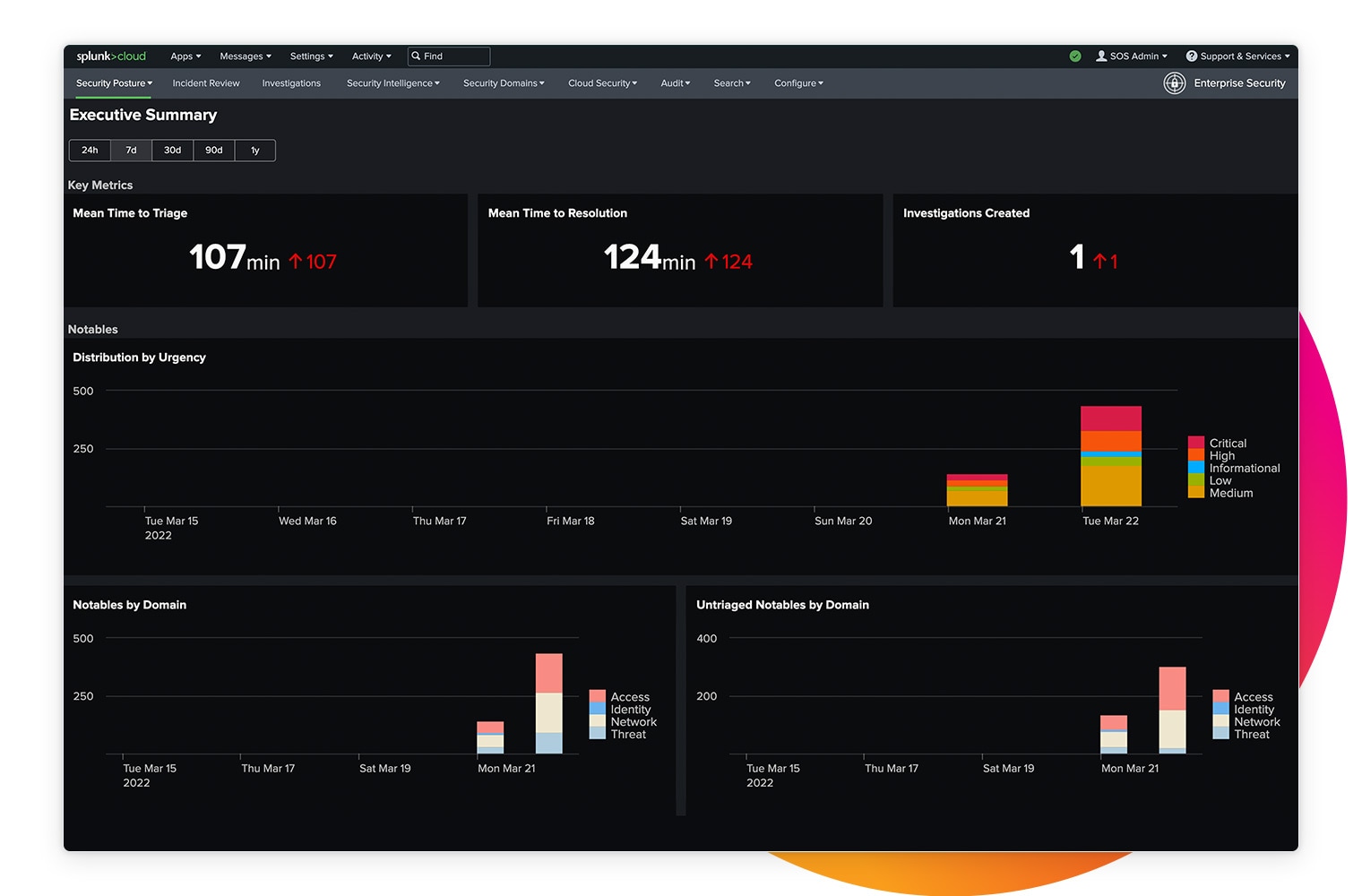
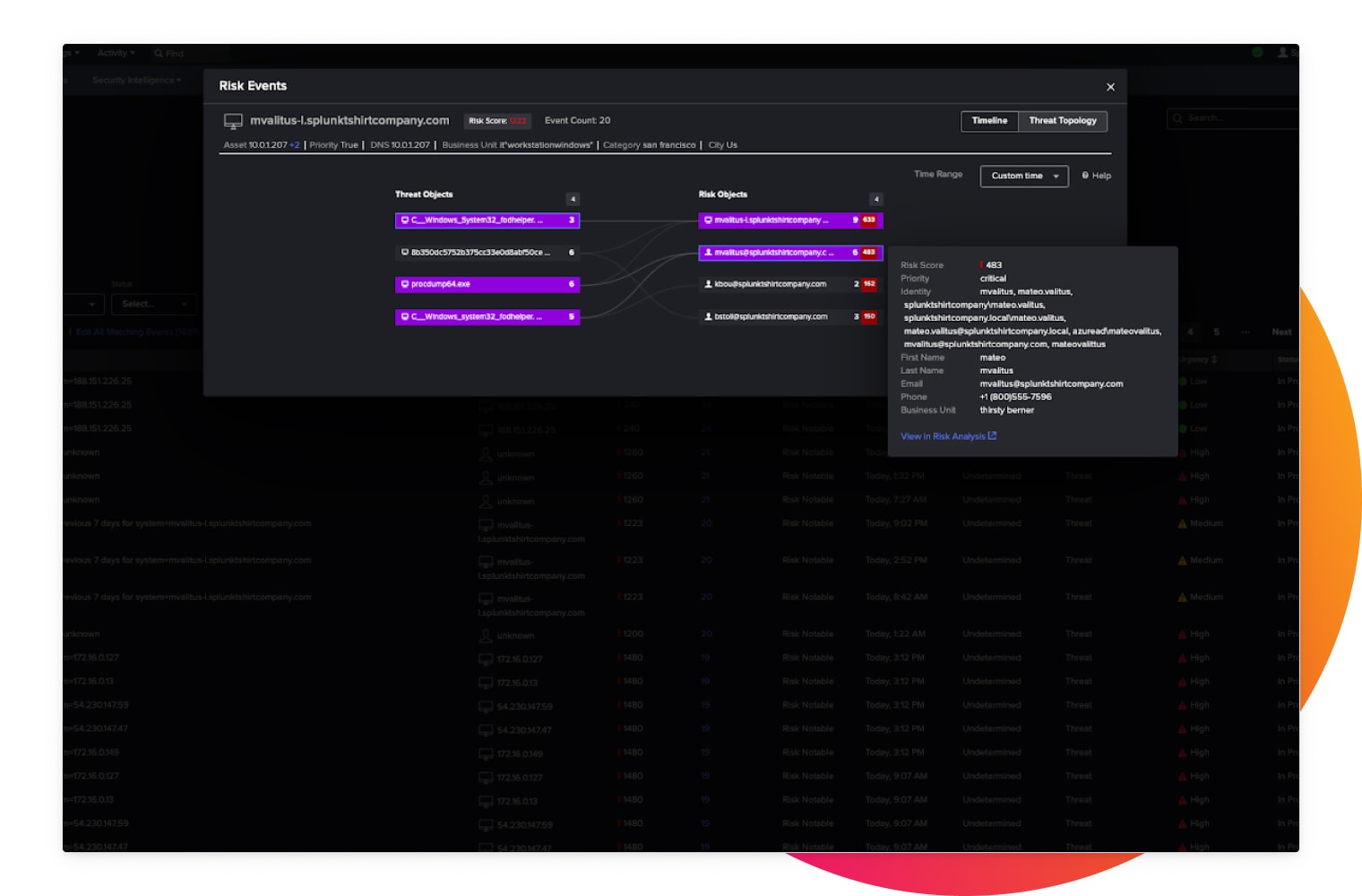
Efficient investigations
Gather all the context you need and initiate flexible investigations with security analytics at your fingertips. The built-in open and extensible data platform boosts productivity and drives down fatigue.
Open and scalable
Built on an open and scalable data platform, you can stay agile in the face of evolving threats and business needs. Splunk meets you where you are on your cloud journey, and integrates across your data, tools and content.
Advanced threat detection
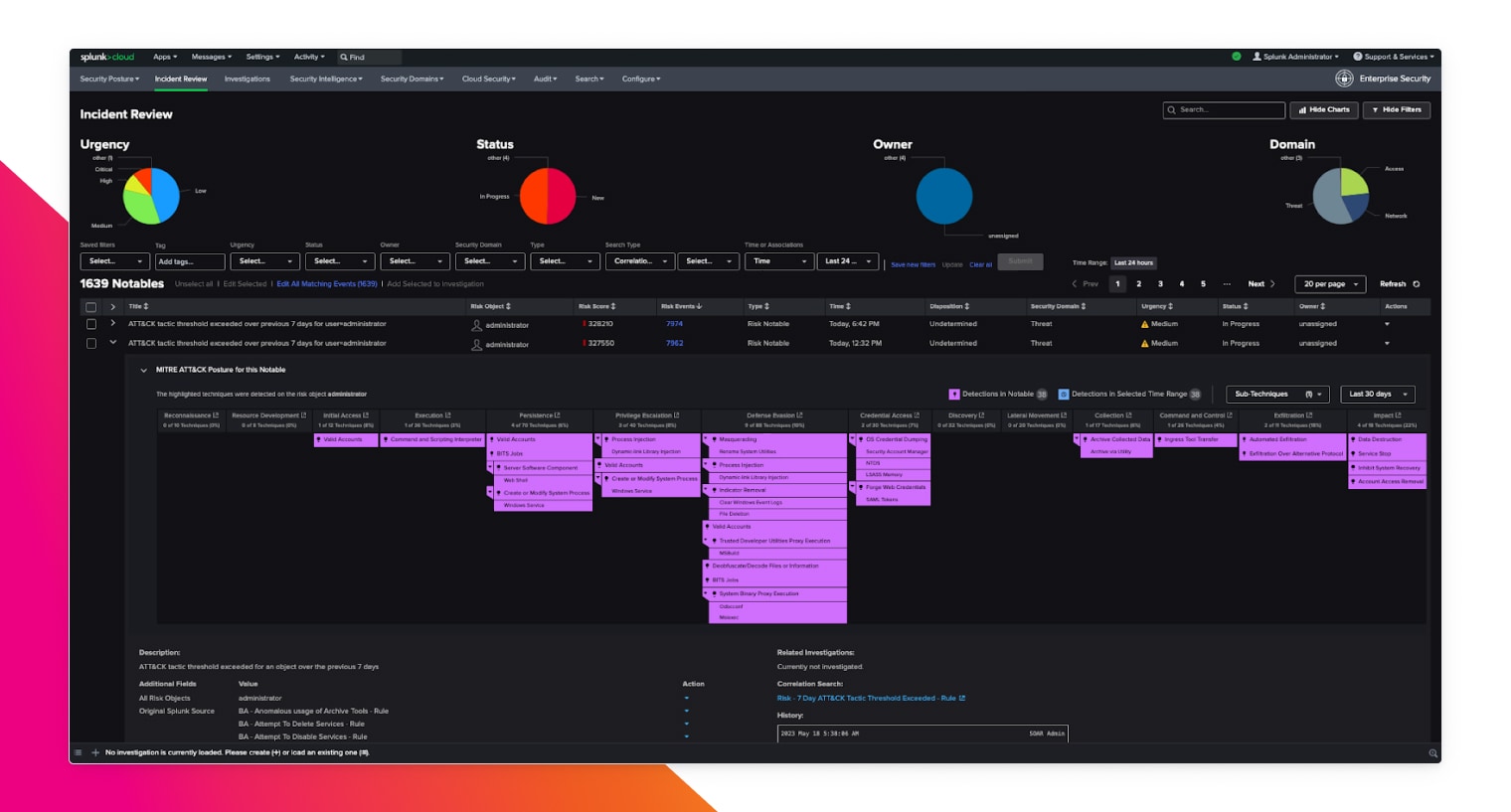
Detect advanced threats with machine learning and 1400+ out-of-the-box detections for frameworks such as MITRE ATT&CK, NIST, CIS 20 and Kill Chain.
Open, extensible data platform
Ingest and monitor tens of terabytes of data per day from any source — structured or unstructured — for full visibility.
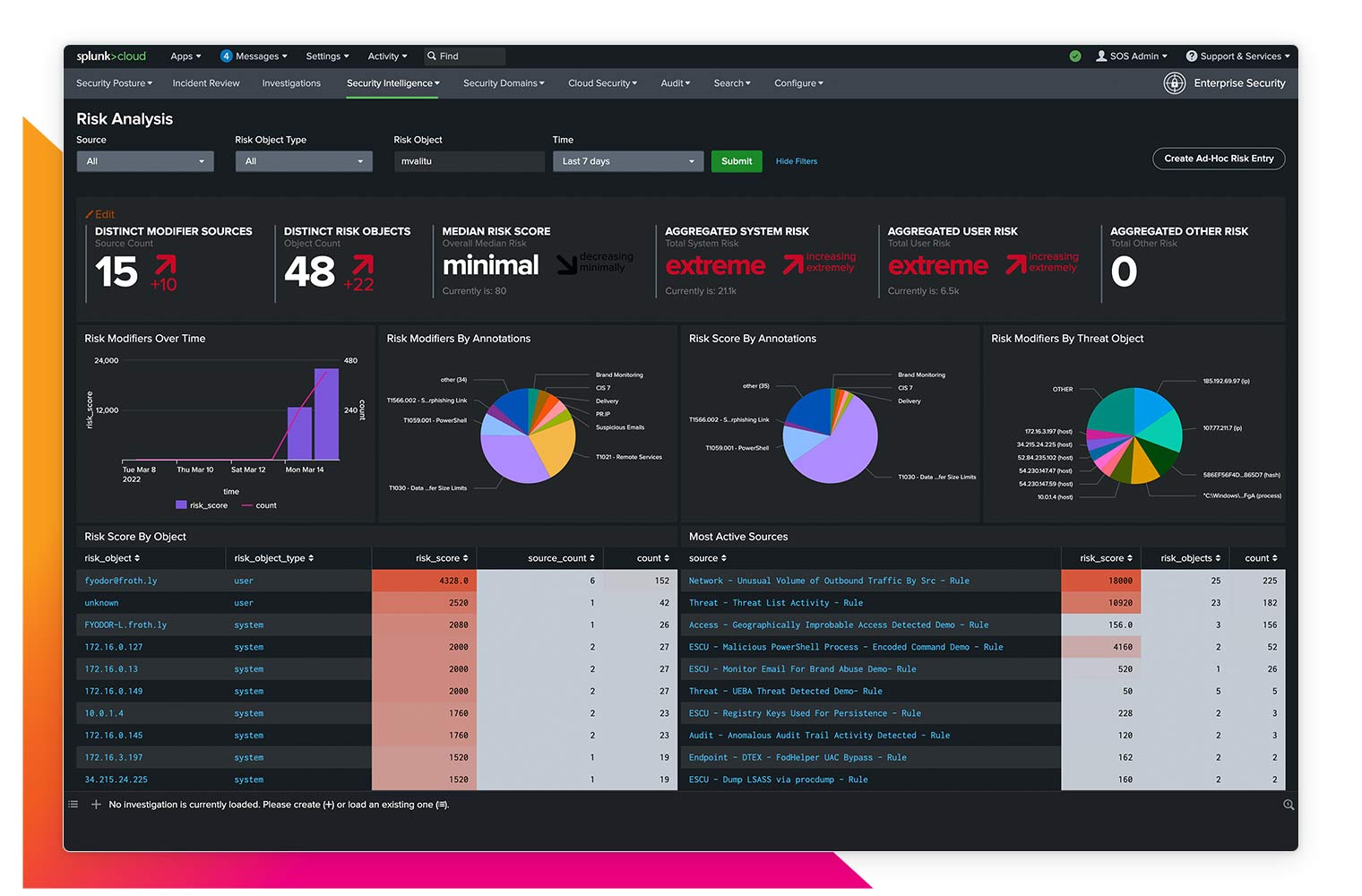
Risk-based alerting
Attribute risk to users and systems, map alerts to cybersecurity frameworks, and trigger alerts when risk exceeds thresholds to conquer alert fatigue.
Integrated intelligence enrichment
Fully investigate security events or suspicious activity by accessing the relevant and normalized intelligence to better understand threat context and accelerate time to triage with Threat Intelligence Management.
Rapid response security content
Get automatic security content updates delivered directly from the Splunk Threat Research Team to help you stay on top of new and emerging threats.
Flexible deployment options
Deploy Splunk Enterprise Security in the way that best meets the needs of your organization — cloud, on-premises or hybrid.


Customer Story

One of Mexico’s Largest Supermarket Chains Improves Response Times by 99%
I’m very happy with Splunk. It’s a powerful and reliable tool with powerful support — the product, the teams and the partners that come with it.


Splunk Attack Analyzer
Automatically detect and analyze the most complex credential phishing and malware threats.
Splunk SOAR
Supercharge your security operations center with orchestration, automation and response.
Splunk Mission Control
Bring order to the chaos of your security operations. Detect, investigate and respond to threats from one modern and unified work surface.
Splunk Security Essentials
Pre-built detections and data recommendations to extend your Splunk solutions.
Splunk App for Fraud Analytics
Power your fraud detections and investigations in Splunk Enterprise Security with this comprehensive anti-fraud solution.
Splunk App for PCI Compliance
Use with Splunk Enterprise, Enterprise Security or Cloud to meet PCI compliance requirements.