This team of security experts develops security content in the form of detections, ML models and SOAR playbooks to help teams address time-sensitive threats and understand attack methods.
Splunk detection engineering process
Learn how the Splunk Threat Research Team develops detections for Splunk security products.

Study Threats
Identify emerging threats and understand how they operate
Generate Datasets
Collect data and use Splunk to parse the data and identify patterns that can be used to detect the threat
Build Detections
Build rules or queries designed to identify specific activity associated with the threat
Test Detections
Run queries against a dataset that simulates attacker behavior to improve accuracy and reduce false positives
Release
Package detections to deliver timely and effective protections against emerging threats to Splunk customers
Power Your SOC with Threat Research

Access the latest detections
Leverage security content through the Enterprise Security Content Updates app, or the Splunk Security Essentials app. You can view the full repository of detections, use cases, and playbooks on the Splunk Security Content site.

Threat research blogs
Read in-depth overviews of various threats and their corresponding detections.
Threat research tools
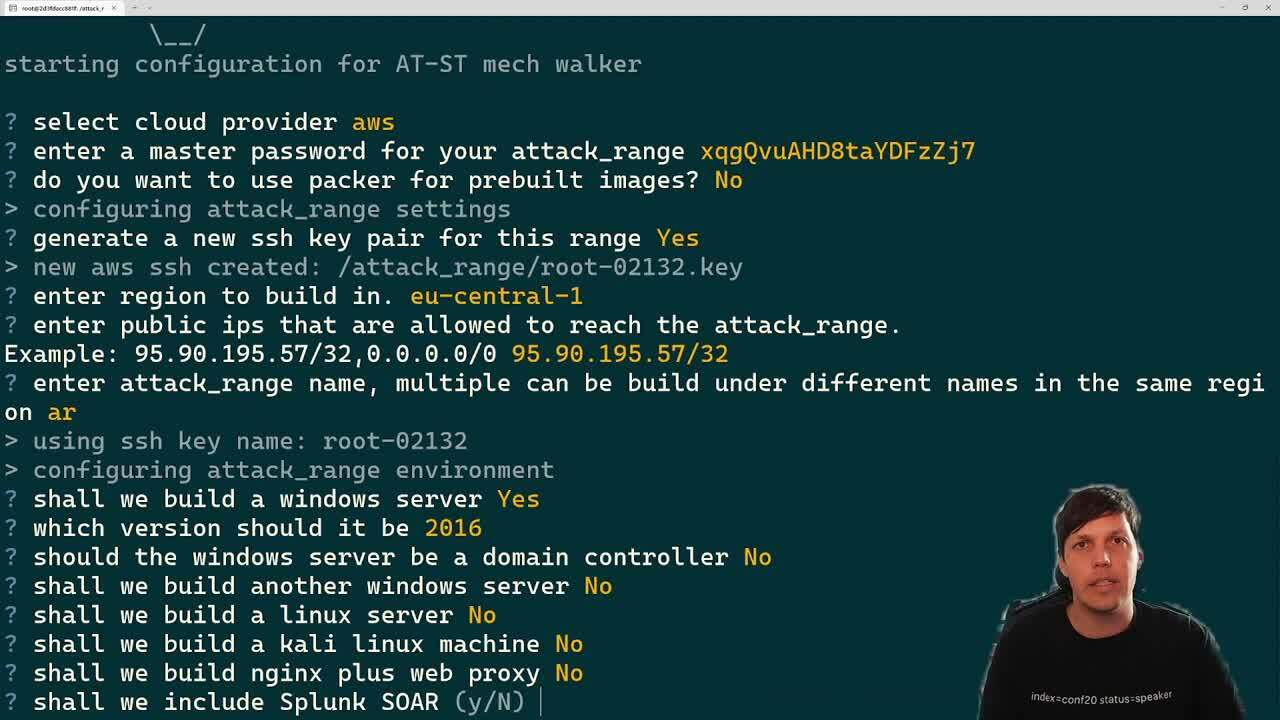
Test your detection searches against cyber attacks in a simulated environment utilizing open source tools from the Splunk Threat Research Team: Attack Range, Attack Data Repository and Melting Cobalt.


Top Cybersecurity Threats
Learn about some of the biggest security threats and how to detect and respond to them with Splunk.
Machine learning for security
Machine and deep learning detections to learn from data, identify patterns, and make decisions to help alert you to threats and anomalous behavior buried within vast amounts of data.
Related security products
Protect your business and elevate your security operations with a best-in-class data platform, advanced analytics and automated investigations and response.
Splunk Attack Analyzer
Automatically detect and analyze the most complex credential phishing and malware threats.
Splunk Enterprise Security
A security analytics solution that moves at the speed of your business with out-of-the-box detections to stay ahead of threats.
Splunk SOAR
Work smarter by automating repetitive security tasks, respond to incidents in seconds, and increase analyst productivity and accuracy to better protect your business.
Splunk Mission Control
Detect, investigate and respond to threats from one modern and unified work surface.
Splunk Security Essentials
Extend the power of the Splunk Platform for enhanced visibility and improved detections with threat research.
Splunk User Behavior Analytics
Secure against unknown threats through user and entity behavior analytics using machine learning.